How to Implement a Systemic Approach to Student Data Security and Privacy
A systemic approach to student data security and privacy should include threat and risk assessment, regular training, and multiple response measures

Tools and ideas to transform education. Sign up below.
You are now subscribed
Your newsletter sign-up was successful
Today, schools are continuously collecting data on the students they serve. This data can be a powerful tool for learning by assisting educators in benchmarking student success, identifying learning gaps, personalizing the learning experience, and more.
The electronic ecosystem schools have developed to accomplish this requires that staff collect, maintain, and support data across countless applications. To further complicate the situation, free or unmonitored applications collect student personal information outside the school's ecosystem. On top of this, hackers continuously test school networks and look for ways to capitalize on security flaws.
Schools have the enormous responsibility of caring for student data and personally identifiable information. Data security and privacy could be one of the most daunting technology tasks educators face, and as we increase the use of technology, the task becomes more challenging every day. This responsibility is bigger than any single school technology department.
School IT departments are working to prevent data theft through deliberate and malicious attacks, data loss through misuse or insufficient protection, and faulty practices in collecting, sharing, storing, and removing data. Combating this rapid evolution requires a commitment to continuous improvement and planning, but how do schools start this journey?
Here are a few ideas that help to support districts.
Review the Law, Standards, and District Policies, and Develop Networks
Data privacy laws are evolving and reflect current threats and knowledge. A district’s first stop should be to review your current state laws and standards. There are many federal laws, such as the Family Educational Rights and Privacy Act (FERPA), Protection of Pupil Rights Amendment (PPRA), Health Insurance Portability and Accountability Act (HIPAA), Children’s Internet Protection Act (CIPA), and Children's Online Privacy Protection Rule (COPPA).
If your state has not adopted a set of standards or laws that regulate student data, you may want to start with the National Institute of Standards and Technology (NIST) Framework. NIST is the framework most states have adopted as the gold standard for data security and privacy. It is used by the government, military, and business.
Tools and ideas to transform education. Sign up below.
You should also consider joining data security and privacy networks in your region, state, or nationally. Many of these groups send regular emails with updates on national trends and security alerts.
Start with the Big Question
It is essential to realize that student data and personal information is part of every aspect of education. Schools need to have regular conversations about data privacy. Start by asking the big questions using the 5Ws of data security and privacy. This includes:
- What data are we collecting?
- Why are we collecting this data?
- Who is collecting and has access to this data?
- When does this data get collected and destroyed?
- Where is this data stored or used?
These simple questions can facilitate in-depth conversation about data in your organization and may ignite some level of healthy debate. These questions will also lead to the development of additional documents.
One vital record to start with is a software and data inventory. A software and data inventory should provide the school a list of software applications, the type of data held in that application, and a determination of each user’s access rights.
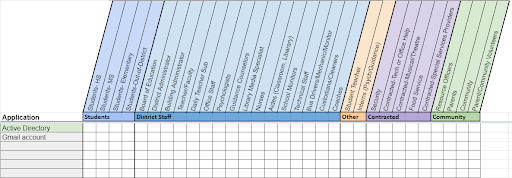
A document such as this helps to uncover important information including where data is stored and who has access to that data. This information is valuable for onboarding and exiting users, for example. Schools should only be collecting the information they need, and users should only have access to the data they need to do their work.
Understand the Threat
To better understand data security and privacy, schools need to analyze the threats they face and the methods used to mitigate these threats. Potential threats have three general components, and districts can address each with specific measures. This includes:
- Preventative measures: Any actions taken to minimize the risk of a data breach, loss, or malicious attack. Preventive measures could include providing regular training, updating applications, or maintaining policies and procedures.
- Detective measures: All ongoing action and technology used to identify potential data breaches, loss, or malicious attacks. Detective measures could include hardware/software alerts, compliance monitoring, or threat detection applications.
- Corrective measures: Any planning or action taken as a result of a specific threat. Corrective measures should include an incident response plan, corrective plan/actions, and recovery plan/actions.
A school responds to each of these measures using administrative controls, technological controls, or physical controls.
- Administrative controls approach data security and privacy by limiting access to specific applications or types of data.
- Technological controls include applications or hardware that monitors the school’s network for potential attacks or threats.
- Physical security protects the physical infrastructure from unauthorized access.
A crosswalk of measures and controls may help schools look holistically at their data security threat measures and controls.

Continuous Professional Learning
It may seem that data security and privacy is a technical problem, but it is much more expansive than this. It is an adaptive challenge that requires constant and continuous human support. It only takes one human intervention to prevent or cause a data breach, so ongoing learning and communication is a must for any organization. Staff training is not a one-time event but a regular reminder of data security and privacy best practices, policies, and procedures. Keeping these practices, policies, and procedures up to date with regular review and refinement will help fight evolving and new challenges.
A data breach, hack, or loss is no longer just a potential risk for an organization; it is inevitable. Preparing with a comprehensive Incident Response Plan and Team is essential. The team should understand the order of command, actions taken based on security threats, communication protocols, and post-activity reflection. Developing tabletop exercises that address your organization’s most significant threats will help make the team ready for any incident.
Know Your Community Tolerance to Risk and Capacity
The continuous balance with technology in schools has always been usability vs. security. The more secure you make a network, the harder it becomes for users to do the work they need to do. No network is 100% safe, but schools must continually improve to address the need for security and privacy. Budget restraints, technical barriers, community support, institutional conditions, or other roadblocks may hinder your ability to manage all of your security concerns in the way you want.
Addressing privacy and security risks can be overwhelming. A tool, such as the Classical Risk Matrix, can help determine the impact of a threat on your organization by analyzing the likelihood of occurrence.
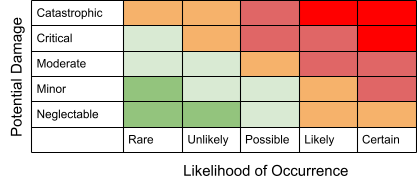
The Classical Risk Matrix considers the potential damage (neglectable, minor, moderate, critical, or catastrophic) this vulnerability provides to the probable occurrence (rare, unlikely, possible, likely, or certain). The greater the potential damage and the higher the likelihood of occurrence, the more significant the impact. The Classical Risk Matrix helps your team prioritize its work. For example, if a threat is certain to happen and would be catastrophic, it would rank high on the task list.
Understanding your organization’s current risk level and your organization’s risk tolerance will help you prioritize your plan and pathway forward. Making your school more secure is a journey, not a destination, and every journey starts with just one step. Make your first step today.
Andrew Taylor is Director of Technology and Professional Learning for Byram Hills School District in Armonk, N.Y.
